Snyk security researcher deploys malicious NPM packages targeting Cursor.com
You can see in the screenshot that the data is then exfiltrated to a website that the attacker owns.
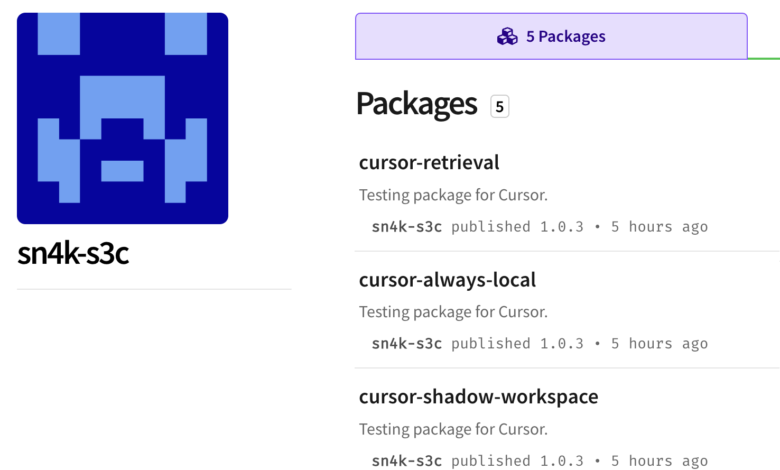
Now, typically, when we see packages like this, they are attempting to perform a dependency confusion attack on a specific company. I don’t know if Cursor.com has a bug bounty program or a specific background. Still, I would suspect that Cursor has several NPM private packages named “cursor-always-local”, “cursor-retrieval”, and “cursor-shadow-workspace”. The person who created these packages is probably hoping that Cursor employees accidentally install these public packages, which will send their data to the attacker-controlled web service.
Luckily, in addition to me seeing these files, the OpenSSF package analysis scanner identified these packages as malicious. OSV generated 3 malware advisories: MAL-2025-27, MAL-2025-28 and MAL-2025-29. You can see the malware advisories here: https://osv.dev/list?q=cursor&ecosystem=npm
Who deployed these malicious packages?
Okay, we know what the packages do when installing them, and we think they target Cursor.com. Who would do this? Well, the answer is in the NPM package metadata.
The user who published the NPM package uses a snyk.io email address for the Snyk Security Labs team. This part of the metadata cannot be faked. The author field in the metadata specifically mentions an employee at Snyk. This part of the NPM package metadata can be faked, but since the publisher is a verified Snyk email, my guess is that this genuinely came from Snyk.